Securing your Google Account
Purpose
This article contains a few suggestions on how to secure your Google Account.
Make use of the Google Account Security Check
When you access your Google Account, on the left hand side there is a link to Security.
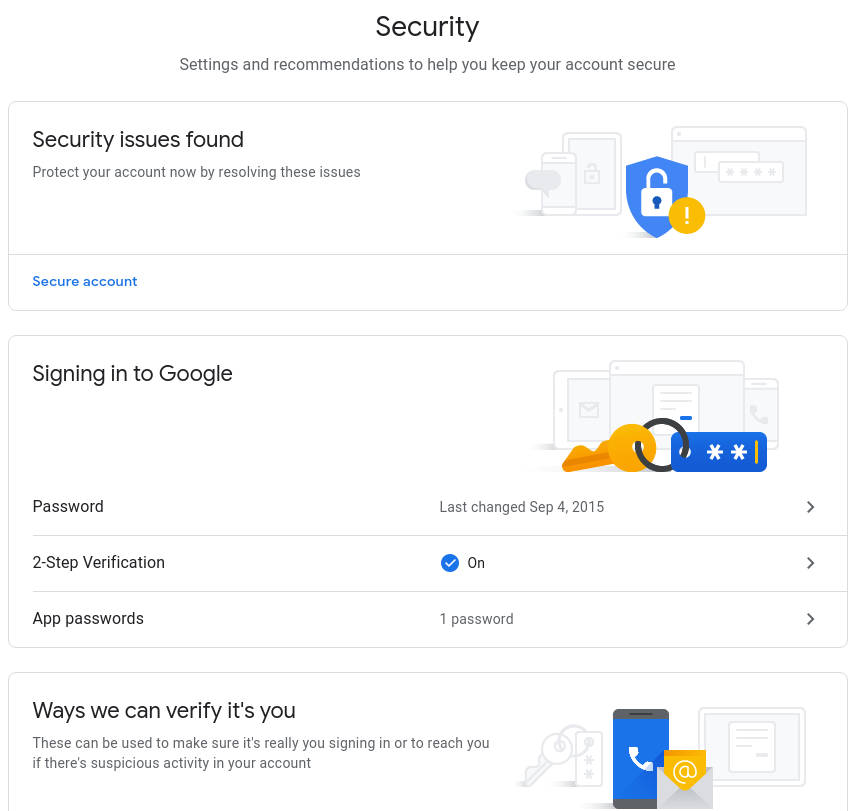
Clicking on that, you should see a window similar to this:
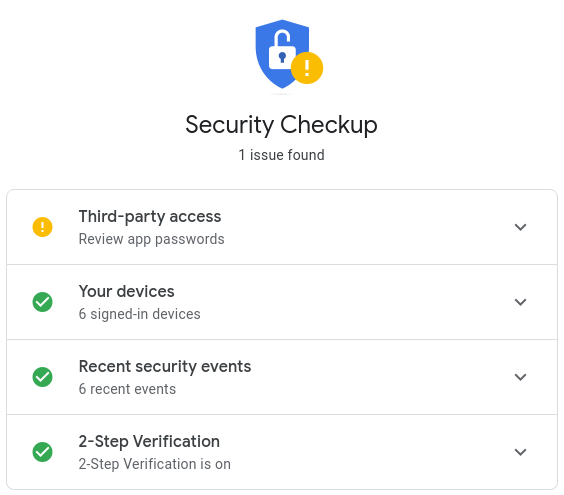
If you see a message like Security issues found, click on Secure Account link...
From here, you can review any potential issues, such as apps accessing your Google Account, devices that are accessing it and verifying 2-Step Verification.
It is always good to review this once in a while to make sure everything looks to be in order.
Set Recovery Information
It is helpful to set a Mobile Phone Number and a secondary email address to help notify you when the account has been accessed by another machine.
One thing to be careful of when you do set this up, is to pay strict attention to the message you are receiving.
The message will identify a general location and device name that is making the attempt.
If this is not something you allowed, you should access your Google Account manually (IE: Don't click the link, go to a browser and go to https://www.gmail.com and log in there and verify the situation.
Set up 2-Step Verification aka Multi-Factor Authentication
You are required by UCSB to setup 2-Step Verification on your school Google Connect account which will help in verifying an actual attempt to connect. It is a good idea to do it on all your other accounts as well.
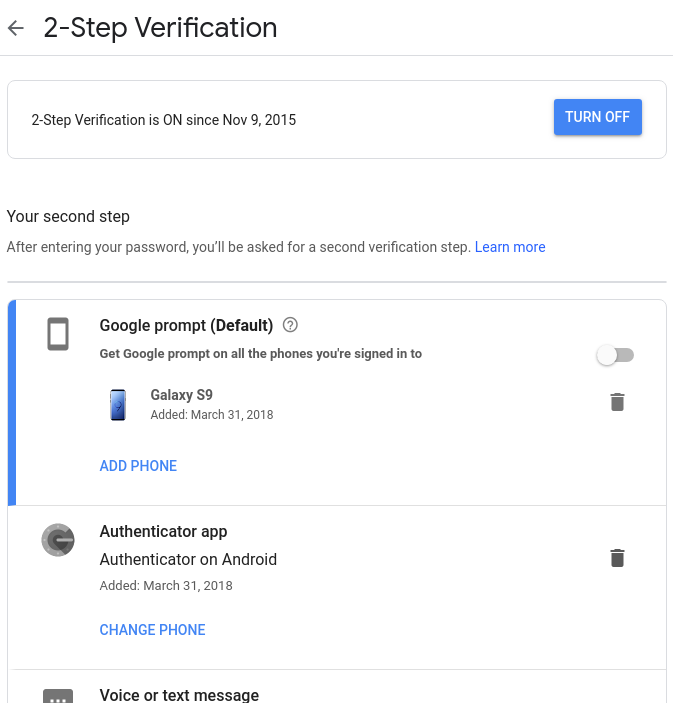
In this example, a user has it set to send a Google Prompt on their Phone to ask for verification.
They also set up the Google Authenticator App as an alternative.
That way if someone has stolen their password, they will not be able to login without having stolen their phone as well or preformed complicated hacking.
For your school Google Connect account we recommend UCSB's DUO, but please be aware campus DUO goes away when you leave UCSB so you need some other form of multi factor authentication such as Google 2SV on personal accounts
For more on this, please refer to Two-Factor, Two-Step or Multi-Factor Authentication.
It is not recommended to setup a text message verification, as SMS systems are becoming less and less secure for situations like this.
Alternative Second Step methods
Google also provides alternative methods for 2-Step Verification such as Backup Codes, which is a printable set of numbers that can be used.
Security Key is another alternative, using systems like YubiKey, which is basically a hardware key that can be plugged into a computer or mobile device to act as a second verification.
Related articles